Cybersecurity threats are not just frequent—they’re evolving in sophistication and impact, making them harder to predict and more costly to ignore. In 2025, experts predict that the cost of cybercrime will reach (and surpass) $10.5 trillion, up from $3 trillion in 2015. This surge underscores the critical need for robust cybersecurity solutions that can keep pace with advanced threats. Progressive Networks has stood at the forefront of cybersecurity innovation, delivering comprehensive services designed to protect businesses from a myriad of cyber dangers.
Understanding Common Cybersecurity Issues
1. Viruses and Malware
Viruses and malware represent some of the most insidious threats to organizational IT infrastructure. They can perform a variety of harmful actions, from deleting or corrupting files to hijacking core computing functions and stealing sensitive information. As digital landscapes evolve, so do the complexity and virulence of these programs. Attackers continuously develop new malware to bypass security measures, with estimates suggesting that there are 450,000 new malware each day. This rapid proliferation demands robust, dynamic security solutions capable of thwarting these ever-evolving threats.
2. Phishing Attacks
Phishing attacks manipulate users into divulging confidential information, such as login credentials and credit card numbers, through deceptive emails and fake websites that mimic legitimate sources. This type of cyberattack is particularly dangerous because it exploits human vulnerabilities rather than technological flaws, requiring a different defensive strategy that involves both technological safeguards and extensive user education. According to reports, phishing is involved in 32% of all data breaches, reflecting its prevalence and danger in the cyber threat landscape.
3. Ransomware
In ransomware attacks, attackers encrypt the victim’s data and demand a ransom for the decryption key. The impact of ransomware extends beyond large enterprises; small and medium-sized businesses are frequently targeted due to their often less stringent cybersecurity measures. In 2020, governmental organizations faced an average ransom demand of $570,857, with actual payments to hackers exceeding $1.75 million, highlighting the severe financial implications.
4. Insider Threats
Insider threats arise from individuals within the organization—whether employees, contractors, or business partners—who have inside information concerning the organization’s security practices, data, and computer systems. These threats are challenging to detect as they involve actors within the organization and can be either malicious or unintentional. Effective strategies to mitigate insider threats include stringent access controls, continuous monitoring of sensitive information, and regular audits of user activities.
5. Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) are complex attacks orchestrated to infiltrate systems and remain undetected for extended periods, allowing attackers to continuously steal data. APTs target specific high-value organizations and entities, including government and military installations, critical infrastructure, and large corporations. They are sophisticated multi-phase attacks that can involve extensive reconnaissance to find vulnerabilities in the target’s security posture. Given their stealth and persistence, APTs pose a significant challenge for detection and response.
Progressive Networks’ Strategies to Mitigate Cyber Threats
1. Advanced Threat Detection
- AI and Machine Learning: Progressive Networks leverages cutting-edge AI and machine learning algorithms to detect anomalies that indicate potential threats in real-time, significantly reducing the time to respond.
- Behavioral Analysis: This involves monitoring network traffic and user behavior to identify unusual patterns that may suggest a security breach.
2. Comprehensive Security Audits
- Vulnerability Assessments: These are crucial for identifying potential entry points for hackers before they can be exploited.
- Penetration Testing: Simulate attacks to test the effectiveness of your security measures and identify areas for improvement.
3. Incident Response Planning
- Preparedness: Progressive Networks helps organizations develop actionable incident response strategies that minimize damage and recovery time.
- Simulation Drills: Conducting regular drills to test these strategies ensures that organizations can act swiftly and effectively when a real incident occurs.
2. Data Protection
- Encryption: Essential for protecting data at rest and in transit, encryption ensures that intercepted data remains unreadable.
- Backup Solutions: Robust backup strategies are vital for data integrity, allowing organizations to recover quickly from cyber incidents.
Securing Your Digital Future with Progressive Networks
In a world where cyber threats are becoming increasingly sophisticated and pervasive, having a robust cybersecurity strategy is not just an option—it’s a necessity. By understanding and addressing the common cyber issues that threaten your organization, Progressive Networks ensures that you stay ahead of the curve. Whether it’s through advanced threat detection, comprehensive security audits, or proactive incident response planning, we provide the tools and expertise needed to protect your business from both current and emerging threats.
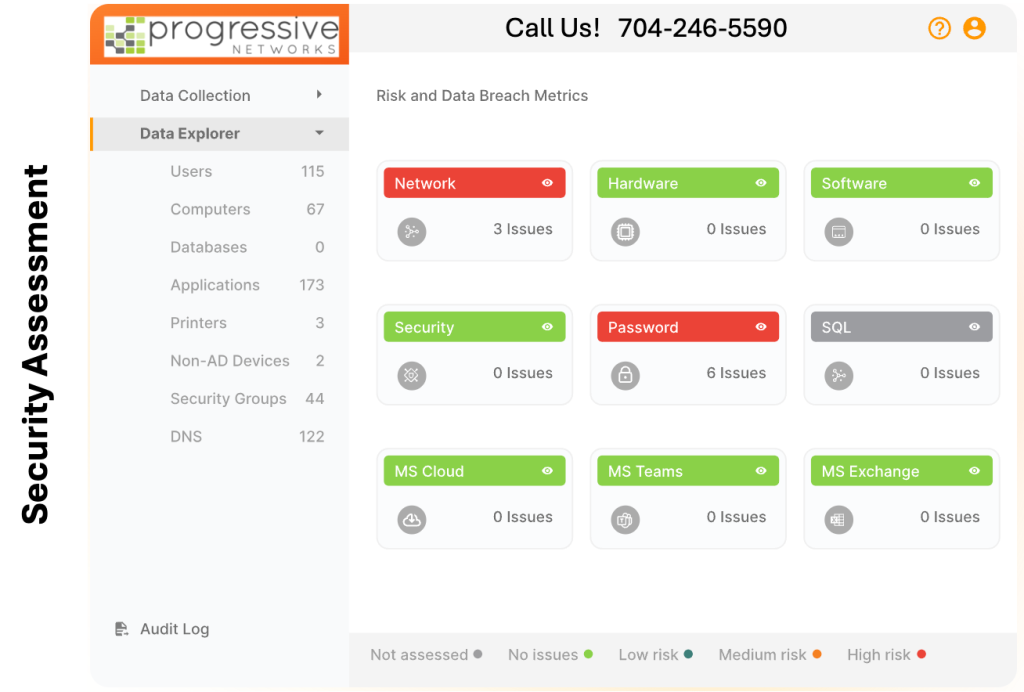
Ready to fortify your defenses? Contact Progressive Networks today for a detailed network assessment and discover how we can help you safeguard your data and secure your digital future. Get a simple report like the one below and let us help you get on the road to protecting you and your client’s data.